SCA
Software Composition Analysis (SCA) is the process of identifying and managing third party open source components included in software applications. SCA aims to assist in identifying and fixing security vulnerabilities at the software component level.
SCA: Result Vulnerability
To ensure the security of your repository code, it is important to display all vulnerabilities present in your project. You can identify software components that have known vulnerabilities and take appropriate action to implement the required mitigation steps. Through this menu, you can increase security and ensure that the repository code is protected from attacks that can exploit existing vulnerabilities. In Result Vulnerability displays three dashboards: SCA Repository Status is the scan status of the repository code, Project Health is the health quality of the repository code, and Repository Vulnerability Found is the number of vulnerabilities found in the repository code.
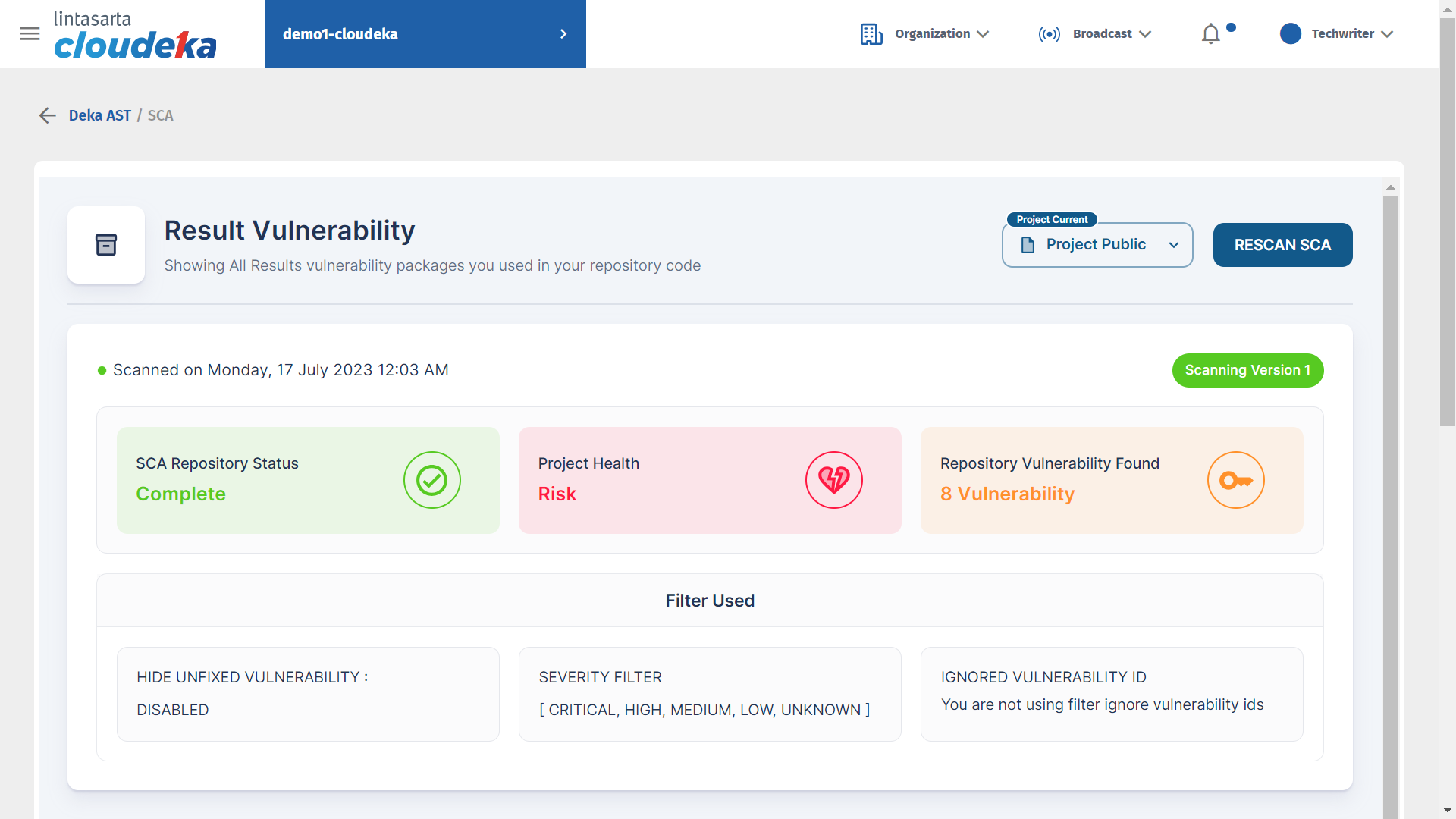
The Issues tab in Result Vulnerability displays a list of vulnerabilities in the repository code that you have. This list identifies potential vulnerabilities in repository code, such as hacking vulnerabilities, network vulnerabilities, and other things. So that you can take appropriate action to fix and improve the security of the repository code to protect the system from attacks and ensure integrity and security.
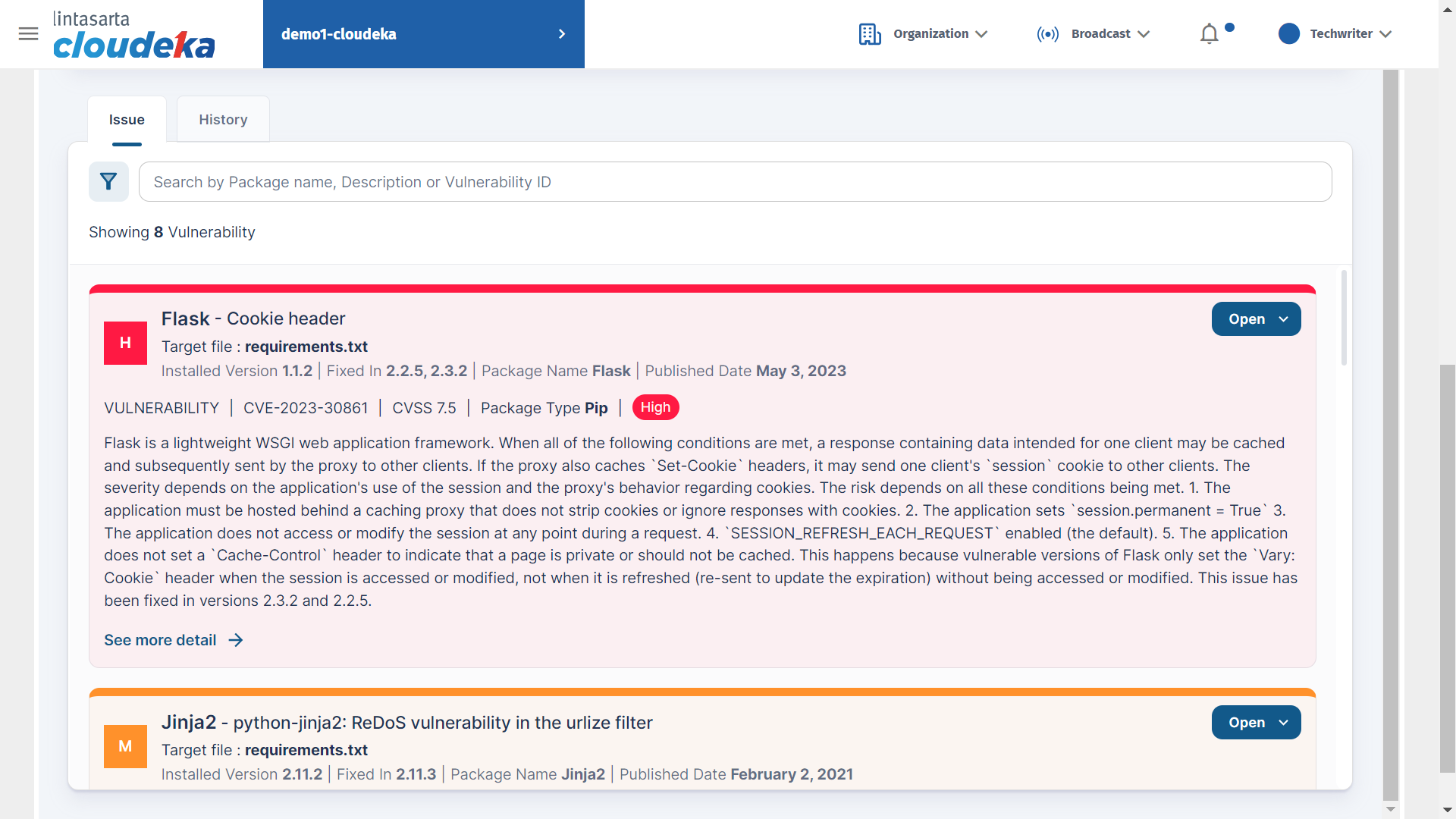
On the History tab of the Result Vulnerability is a history of changes associated with vulnerabilities that are identified in your repository code. The history tab is classified as three of which New Vulnerability is a new vulnerability found when successfully scanned, Fixed Vulnerability is a fixed vulnerability, and Rediscovered Vulnerability is a vulnerability recovered when the scan is repeated. To view details of the new vulnerabilities found during the scan click See more Details to view the severity and explain why this could be a problem.
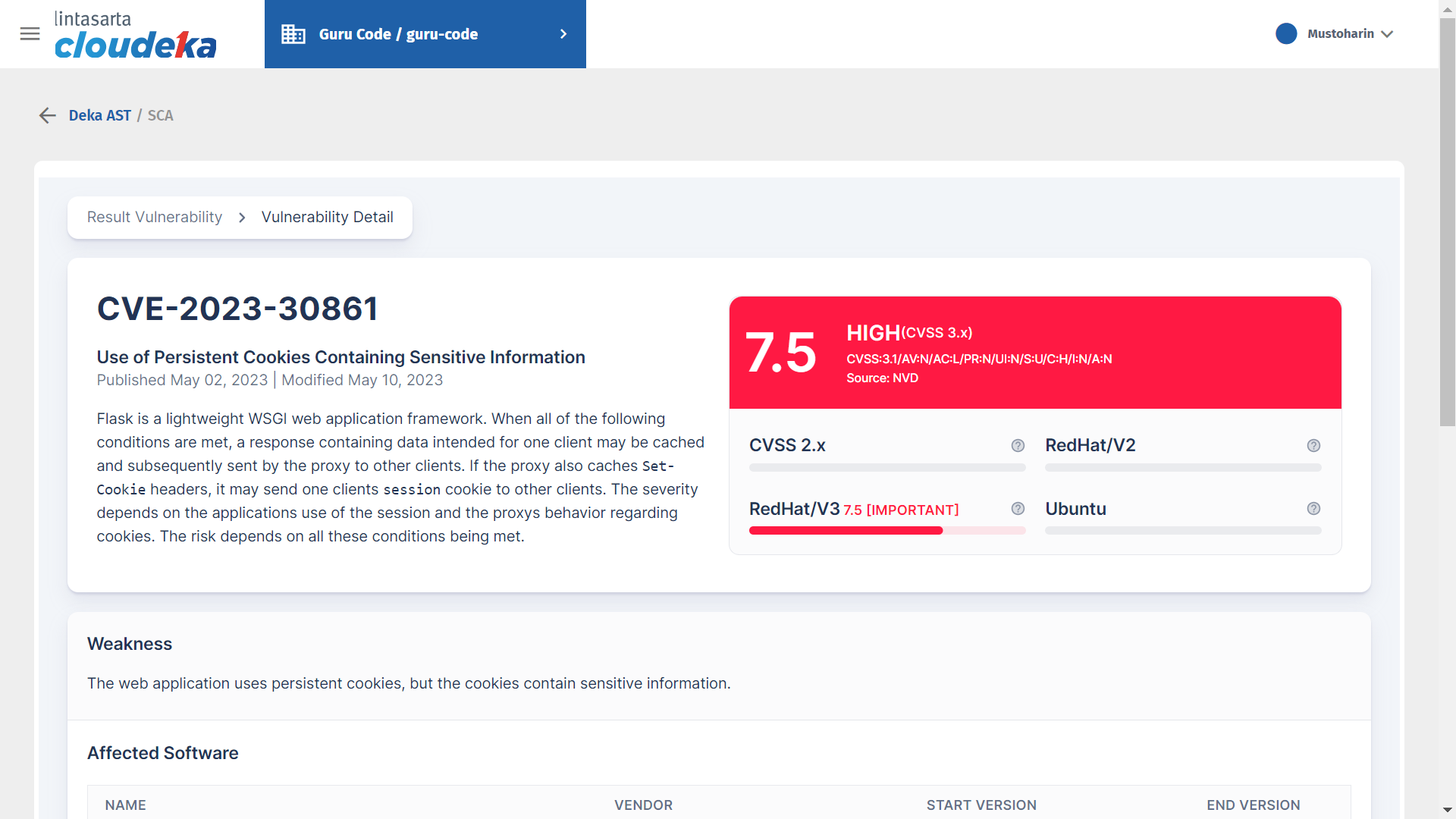
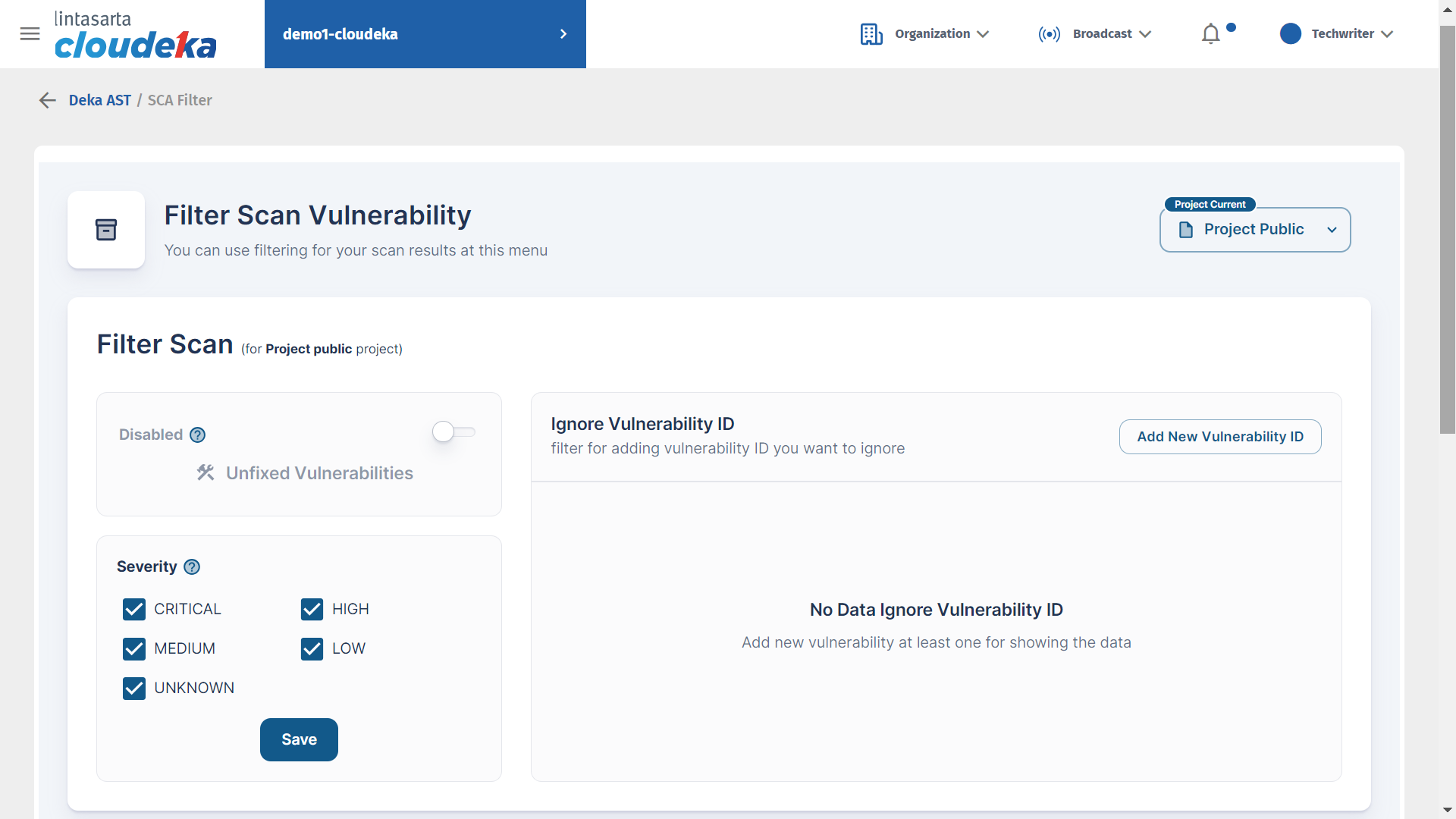
SCA: Filter Scan Vulnerability
On the Scan Vulnerability Filter menu, there are three dashboards: Unfixed Vulnerabilities to detect uncorrected vulnerabilities, user Severity can select a severity level to display on the Result Vulnerability page, and the user ID Ignore Vulnerability ID can ignore the vulnerability by adding a new vulnerability ID.
Last updated
