Configuration Inbound Rule
The Security Group at Deka Harbor has determined the port you can use. If you enter a port that is not specified, the message “The specified port is not allowed. Please check the port in the frontend configuration of the Load Balancer.” For a more detailed explanation of the ports that can be used, see Table below.
443
This port can be used for secure communication via the HTTPS (Hypertext Transfer Protocol Secure) protocol.
6443
The port used by kubernetes to provide a secure server API management and authentication interface.
80
The port is used for unencrypted communication via the HTTP protocol but information sent via this port is not encrypted so it is not safe for use in environments that require data security.
3100
This port can be used for various services depending on the configuration.
The following is a guide to setting up the configuration for inbound rules on Deka Harbor:
On the Cloudeka portal service page, select the Deka Harbor menu on the Platform.
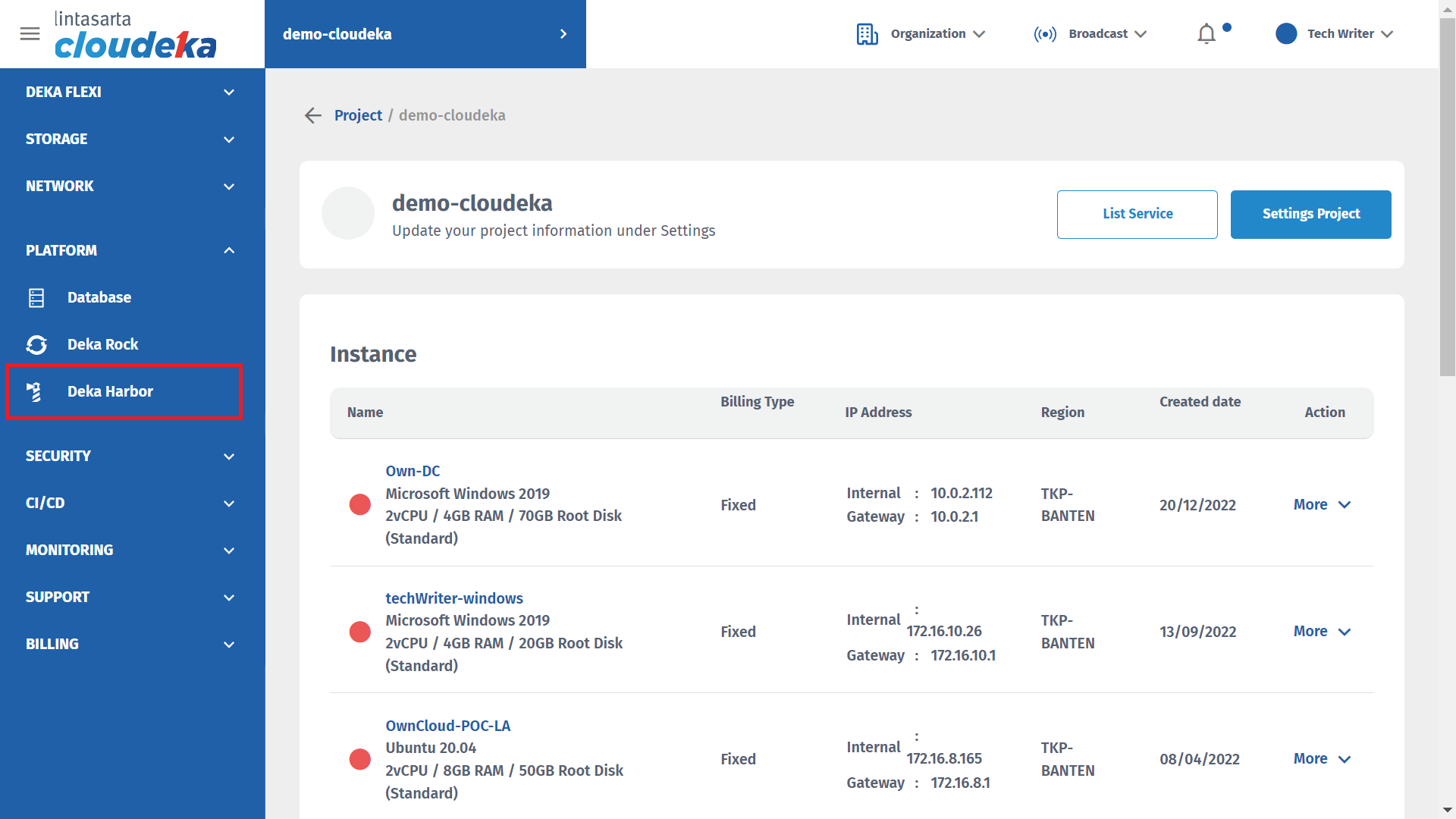
Select the cluster to be added to configure the Load Balancer by clicking More in the Action column then clicking Details.
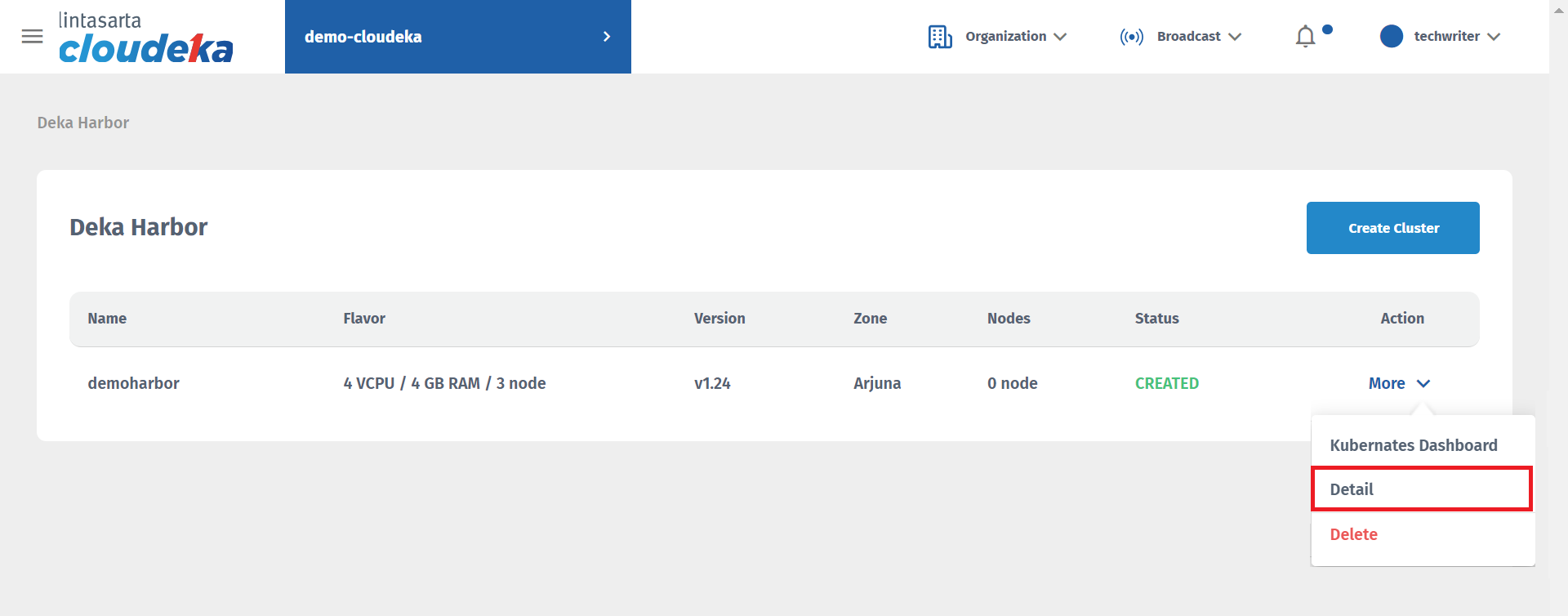
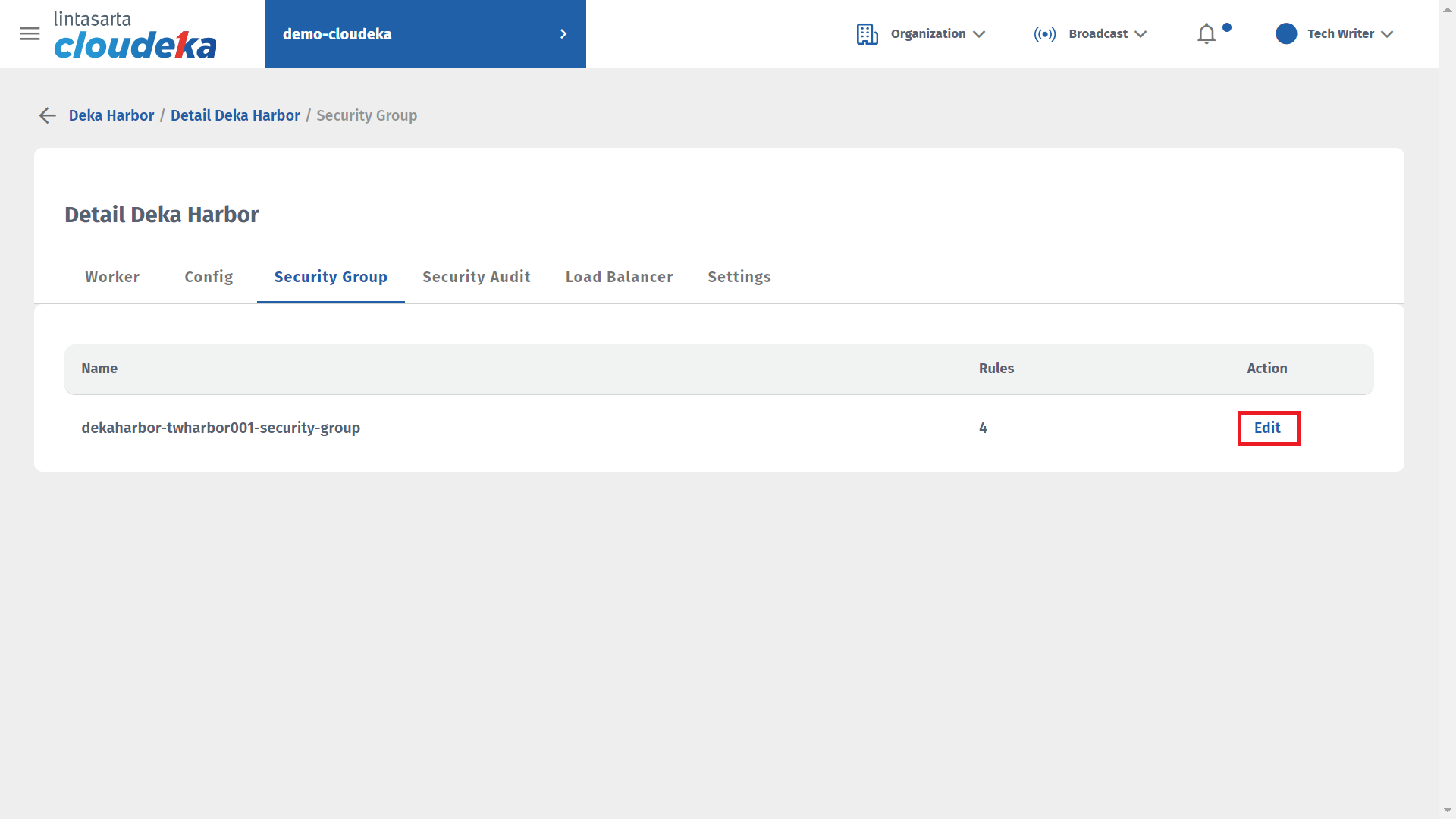
Select the Security Group tab then press the Edit button.
Fill in the data to be changed.
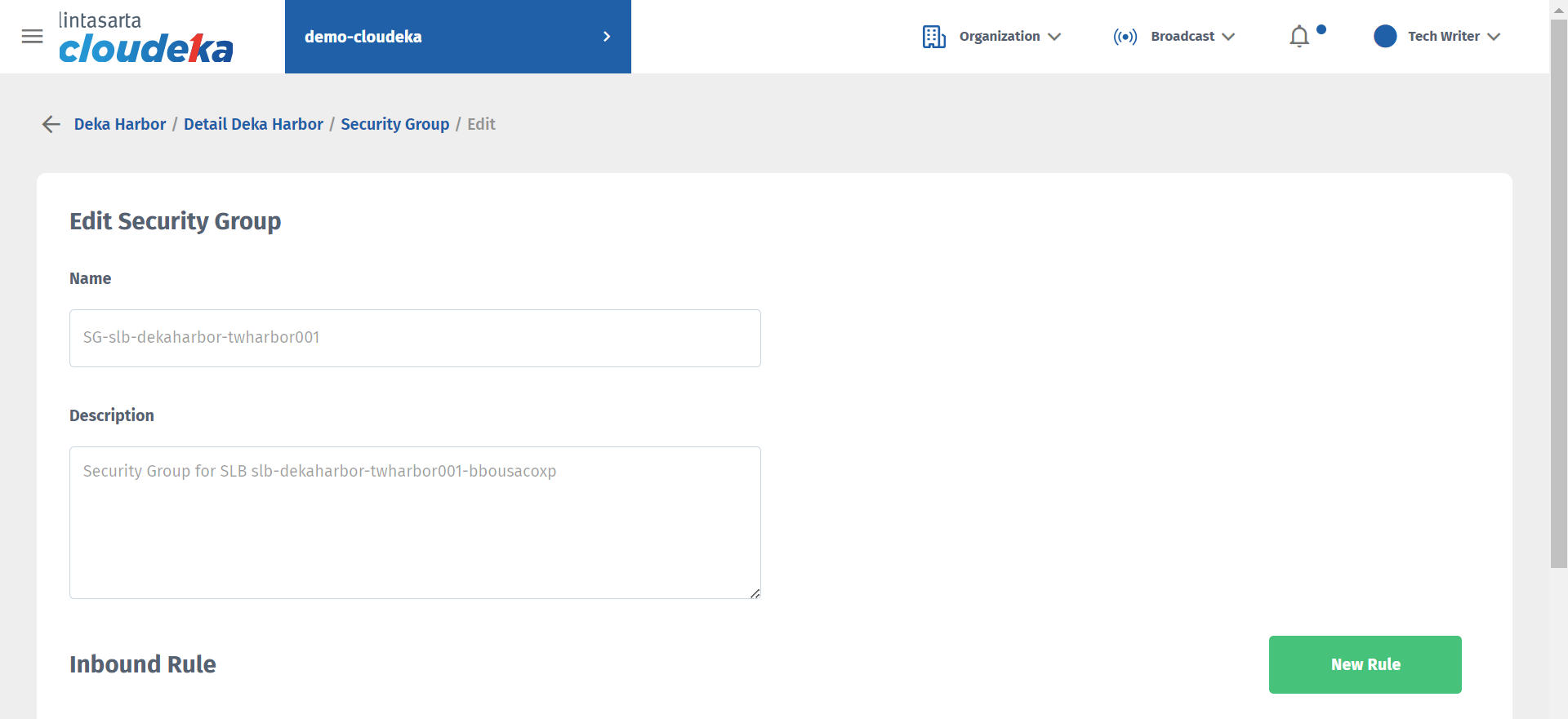
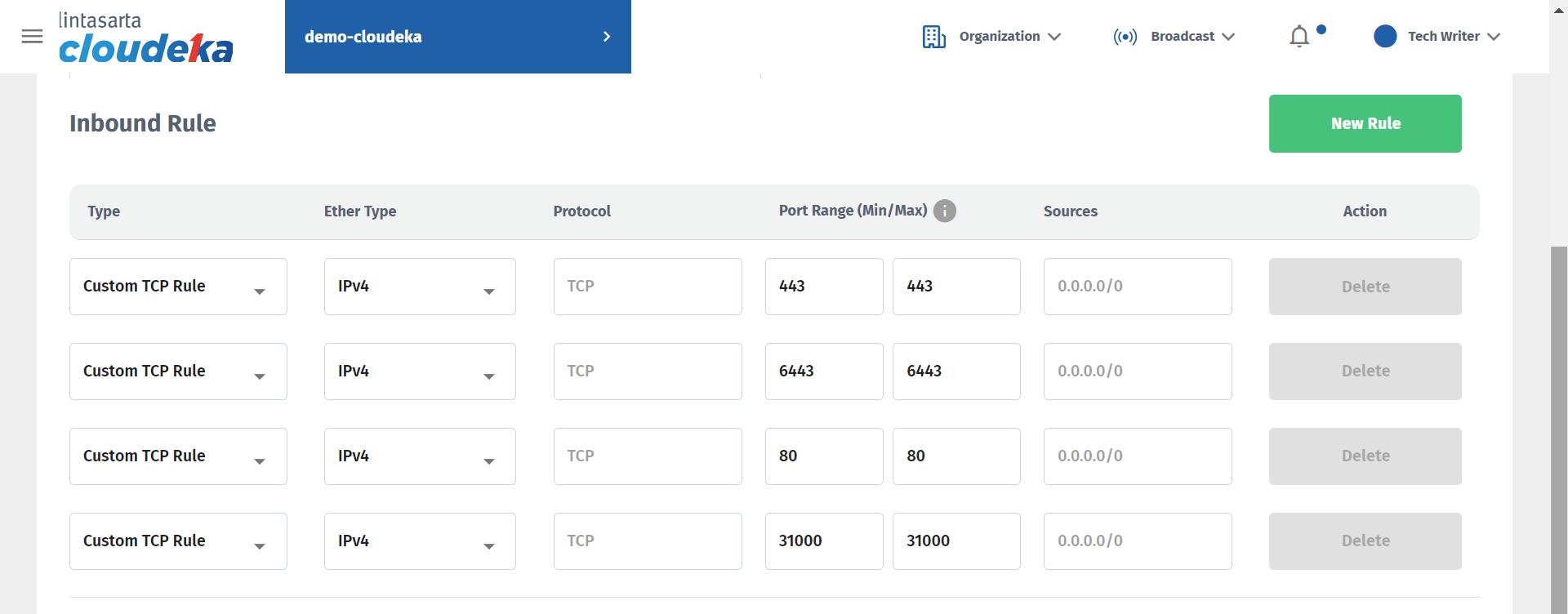
Protocol Type
Supported protocols are: - SSH, - HTTP, - HTTPS, - Custom TCP Rules, you can customize TCP rules and specify specific ports according to your needs. - Custom UDP Rules, you can customize udp rules and specify specific ports according to your needs. - All ICMP Rules.
Ether Type
Type of IP used, select IPv4 and IPv6.
Sources
For inbound rules, which allow you to limit the source of inbound connections by entering individual IP addresses or entering a CIDR. for example, enter CIDR 182.23.45.0/24 into the rule to allow inbound traffic from IP addresses between 182.23.45.0 and 182.23.45.255. Or leave the field blank if you want to allow from any source.
Press the Save button to save changes.
Last updated
