Edit Security Firewall Rule
This guide is used if there is Security Firewall Rule data that you want to change.
On the Security page, there are columns Name, Applied to, Rules and Action. In the action column, click Edit.
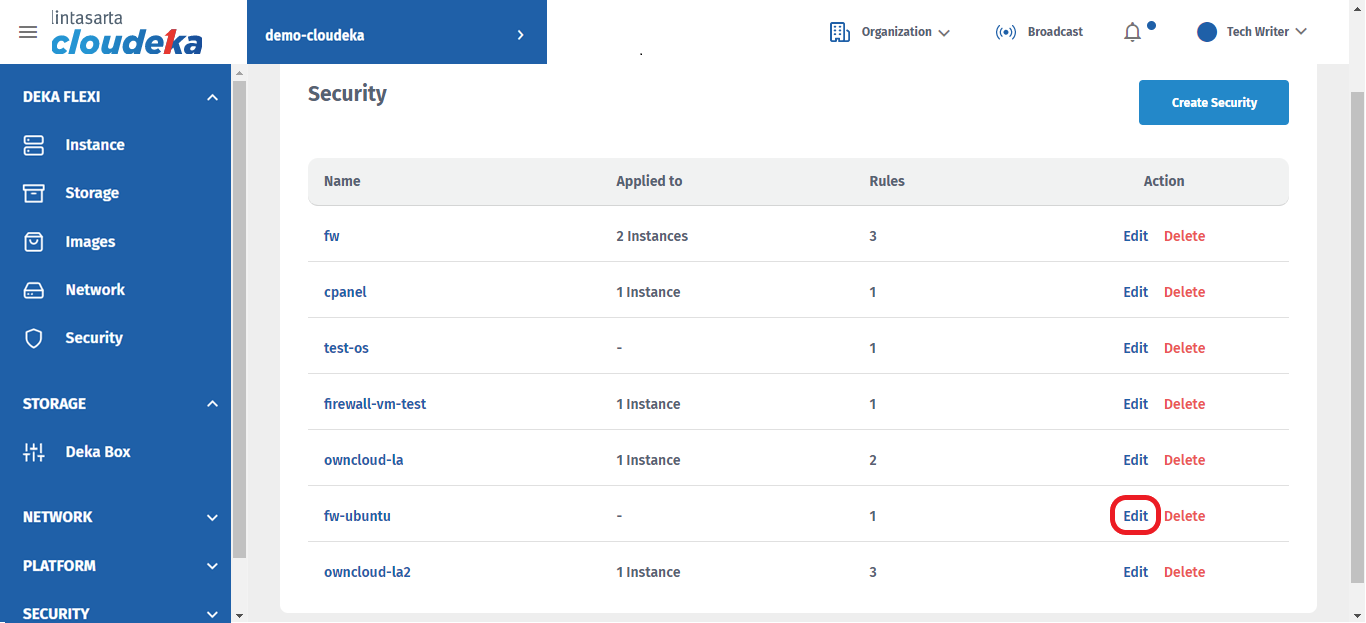
Fill in the data you want to change such as:
Name
The name of firewall rules
Inbound Rule
Define the traffic allowed to the instance on which ports and from which sources
Outbound Rule
Define the traffic allowed to leave the instance on which ports and to which destionations
Protocol type
Supported protocols are: - SSH - HTTP - HTTPS - Custom TCP Rule, you can customize tcp rules and define specific ports according to your needs - Custom UDP Rule, you can cuztomize udp rules and define spesific ports according to your needs - All ICMP Rule
Ether type
Types of IP address, choose IPv4 or IPv6
Port Range
For the custom tcp and udp protocols rule, you can specify: - A single port - A range of ports by entering the starting and ending ports, eg. 3000-4000 - All ports by leaving the field blank
Source
For inbound rules, which lets you restrict the source of incoming connections by entering the individual IP address or entering a CIDR. for example, enter the CIDR 182.23.45.0/24 to a rule that allows incoming traffic from any IP address between 182.23.45.0 and 182.23.45.255. or leave the field blank if you want to allow it from any source.
Destination
For outbound rules, which lets you restrict the destionation of outgoing connections by entering individual IP address or entering CIDR or leave the field blank if you want to allow it to any destination
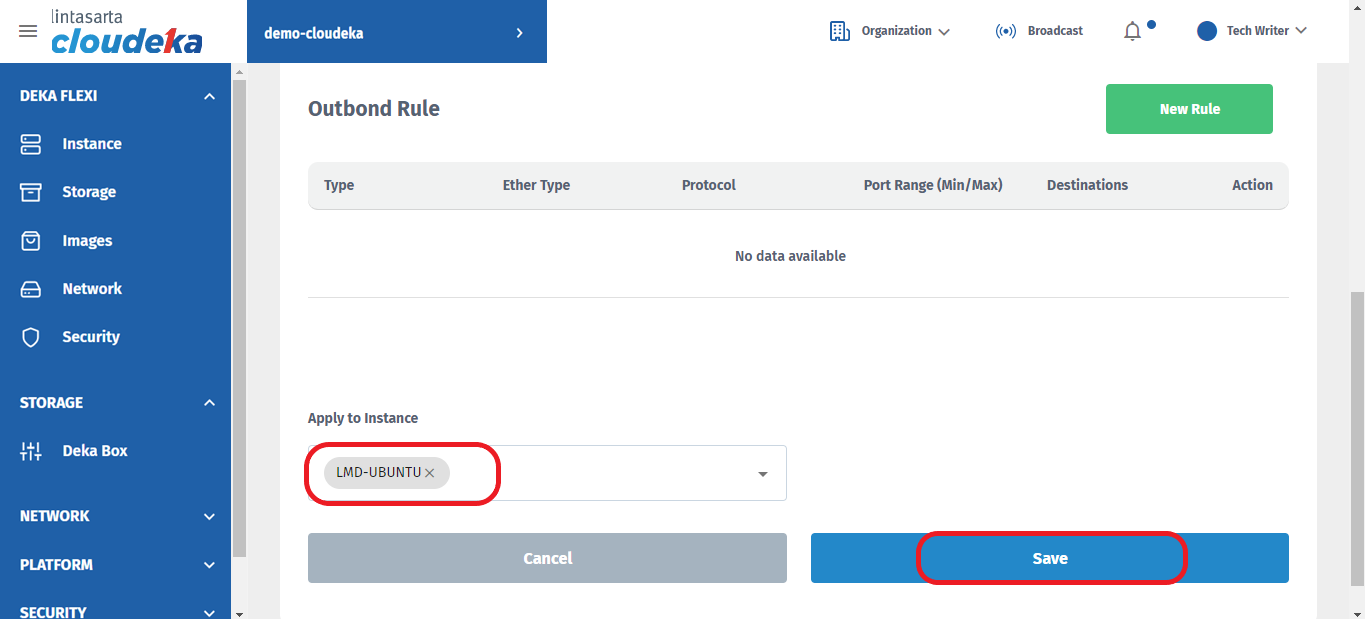
Apply to Instance
Choose a specific instance to that you want to apply the rule.
Click the Save button if you want to continue changing the firewall data or cancel if you don't want to continue the process.
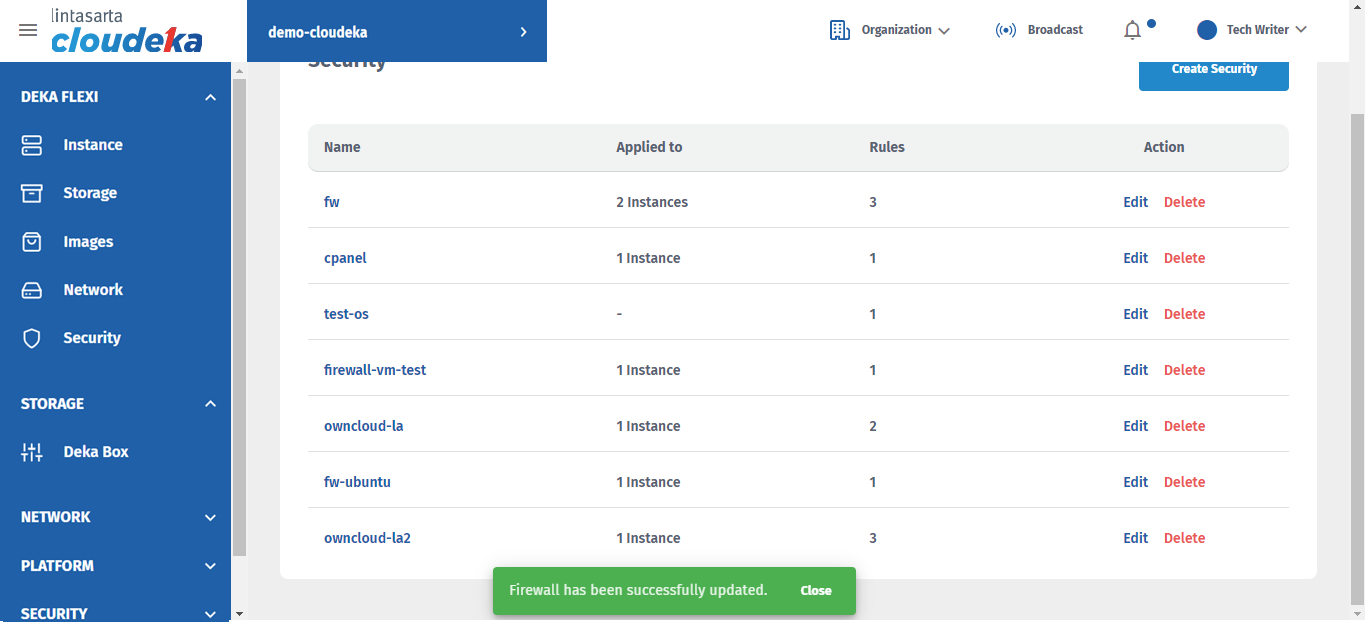
There will be a notification if the Firewall has been successfully changed "Firewall has been successfully updated".
Last updated
