Security Group
Security Group allows or denies connections to or from virtual machines based on configurations you specify. When you create a rule in security, you define a set of components that determine what the rule does. Components allow you to target specific types of traffic, based on traffic protocol, destination port, source, and destination. In the Security Group, you can create, update data, and delete incoming or outgoing rules in Deka ROCK.
Add Inbound/Outbound Rule
Following are the steps to create entry or exit rules on Deka ROCK: On the Cloudeka portal service page, select the Deka ROCK menu on the Platform.
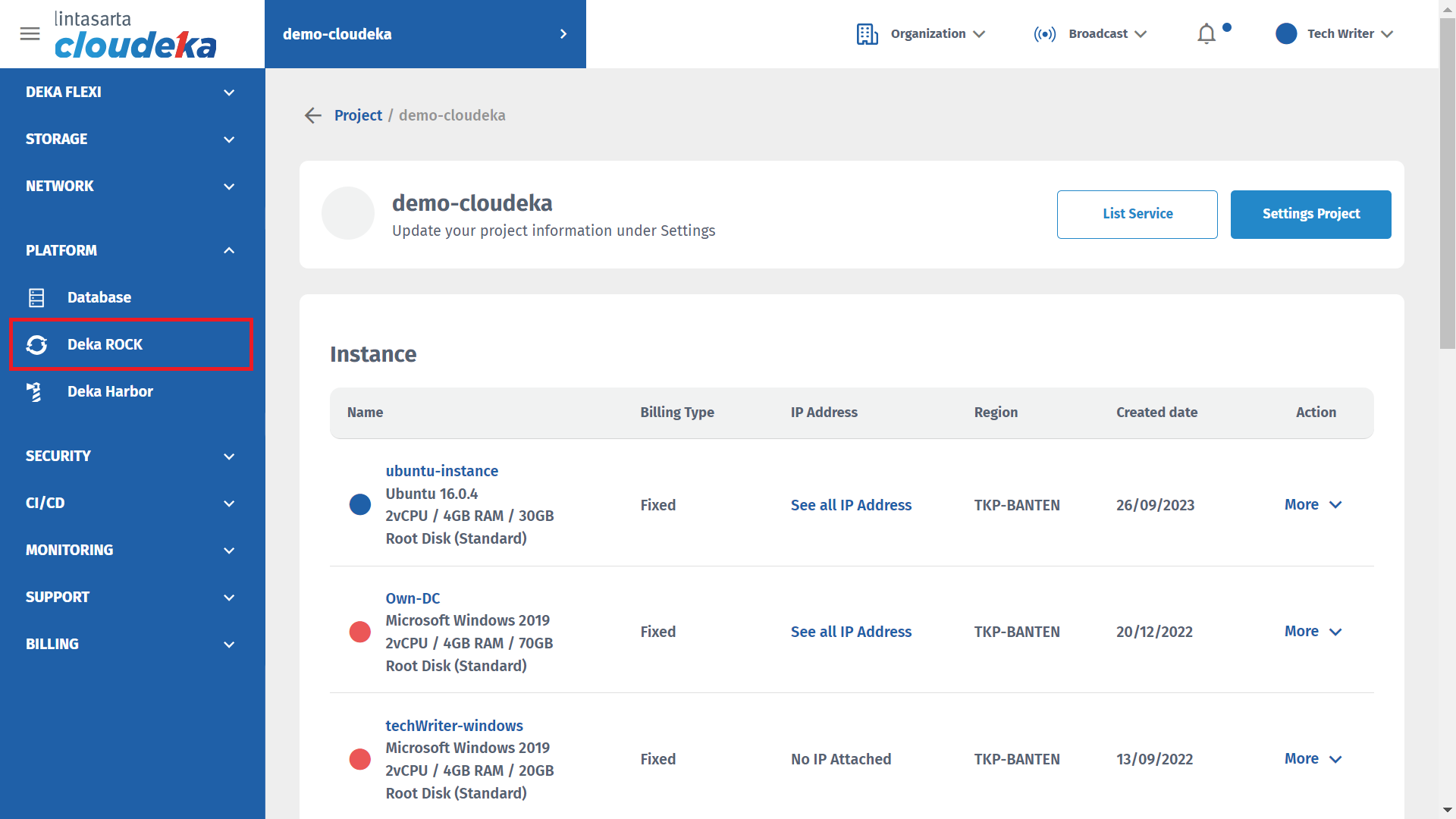
Press the More button then select the Details button.
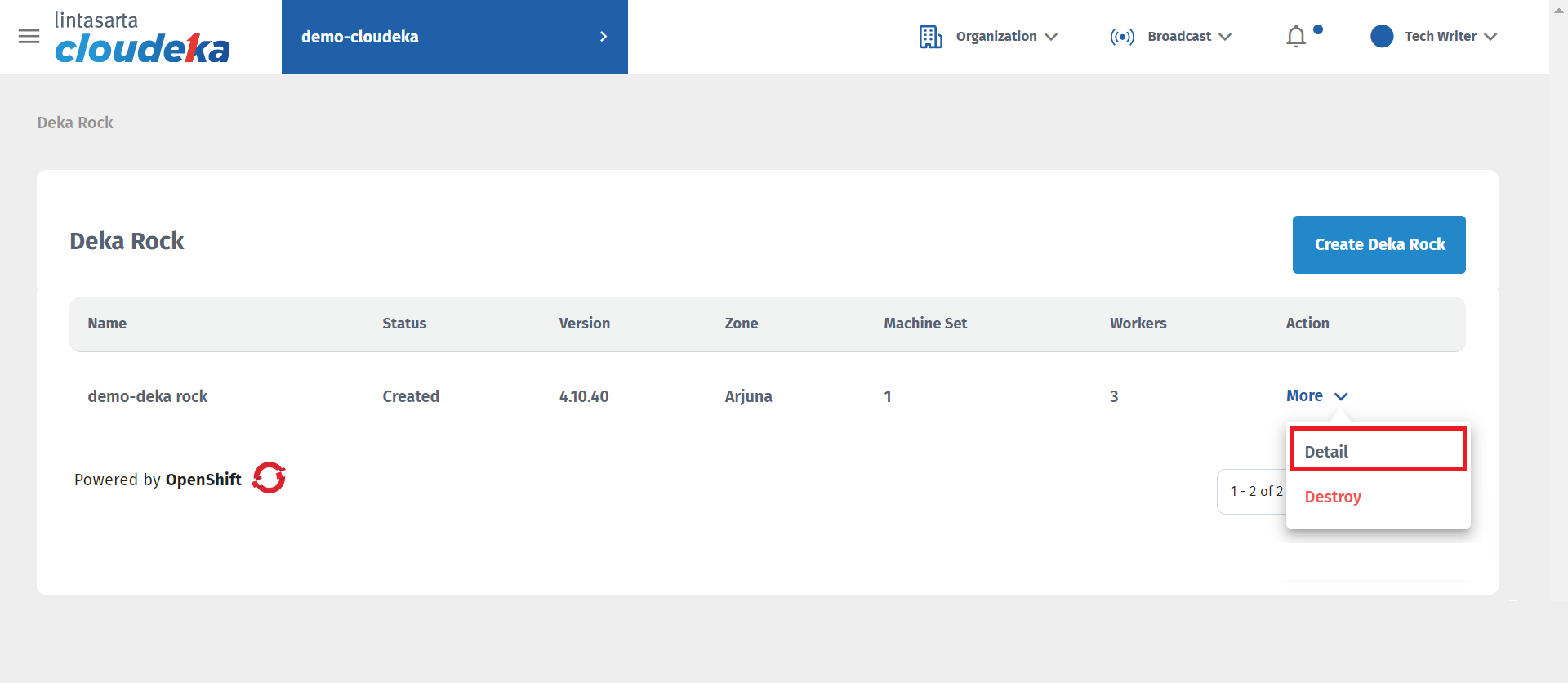
Select the Security Group tab.
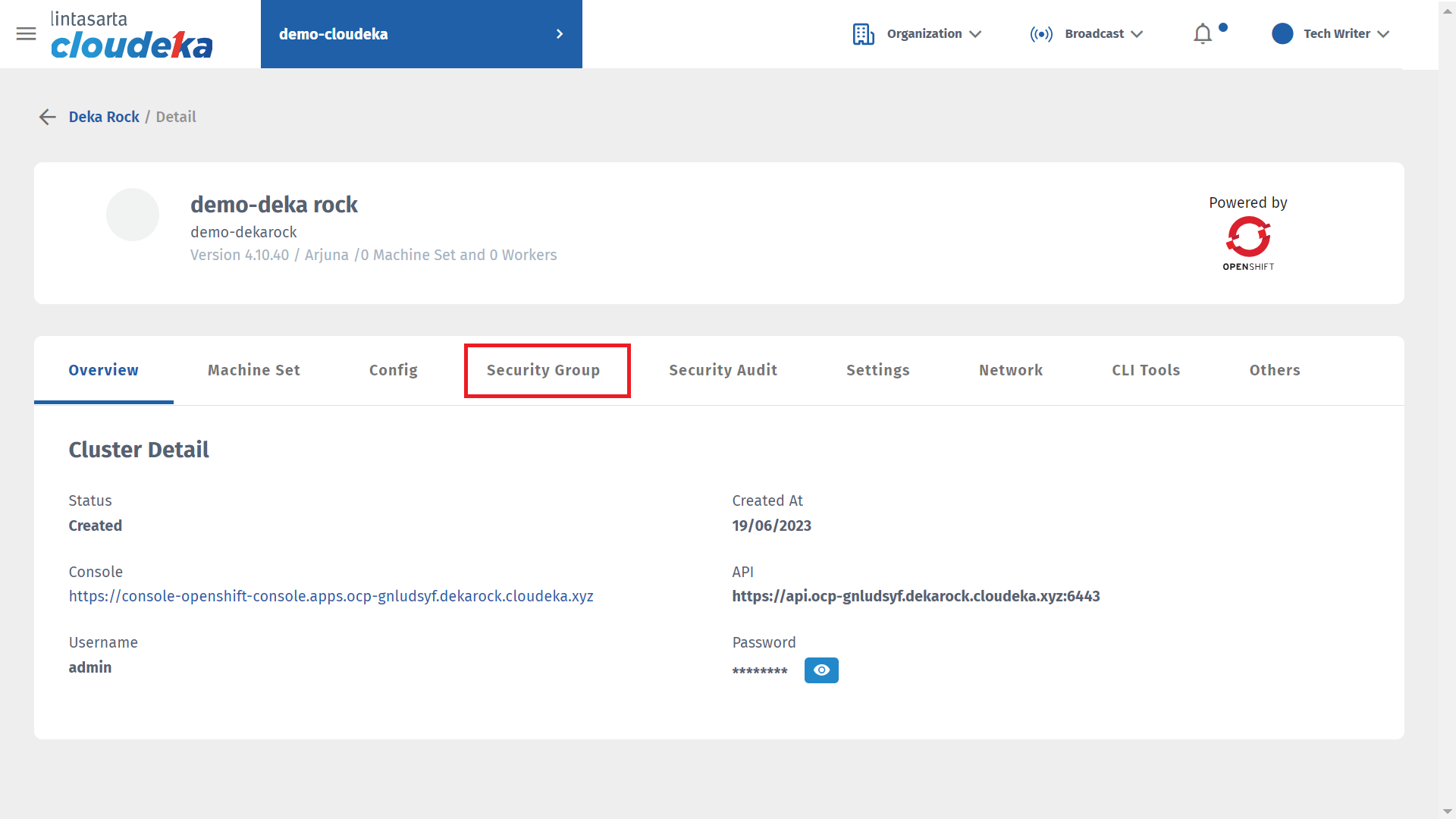
Press the New Rule button on (a) to add an inbound rule or (b) to add an outbound rule.
The Add Role window appears, fill in the available columns.
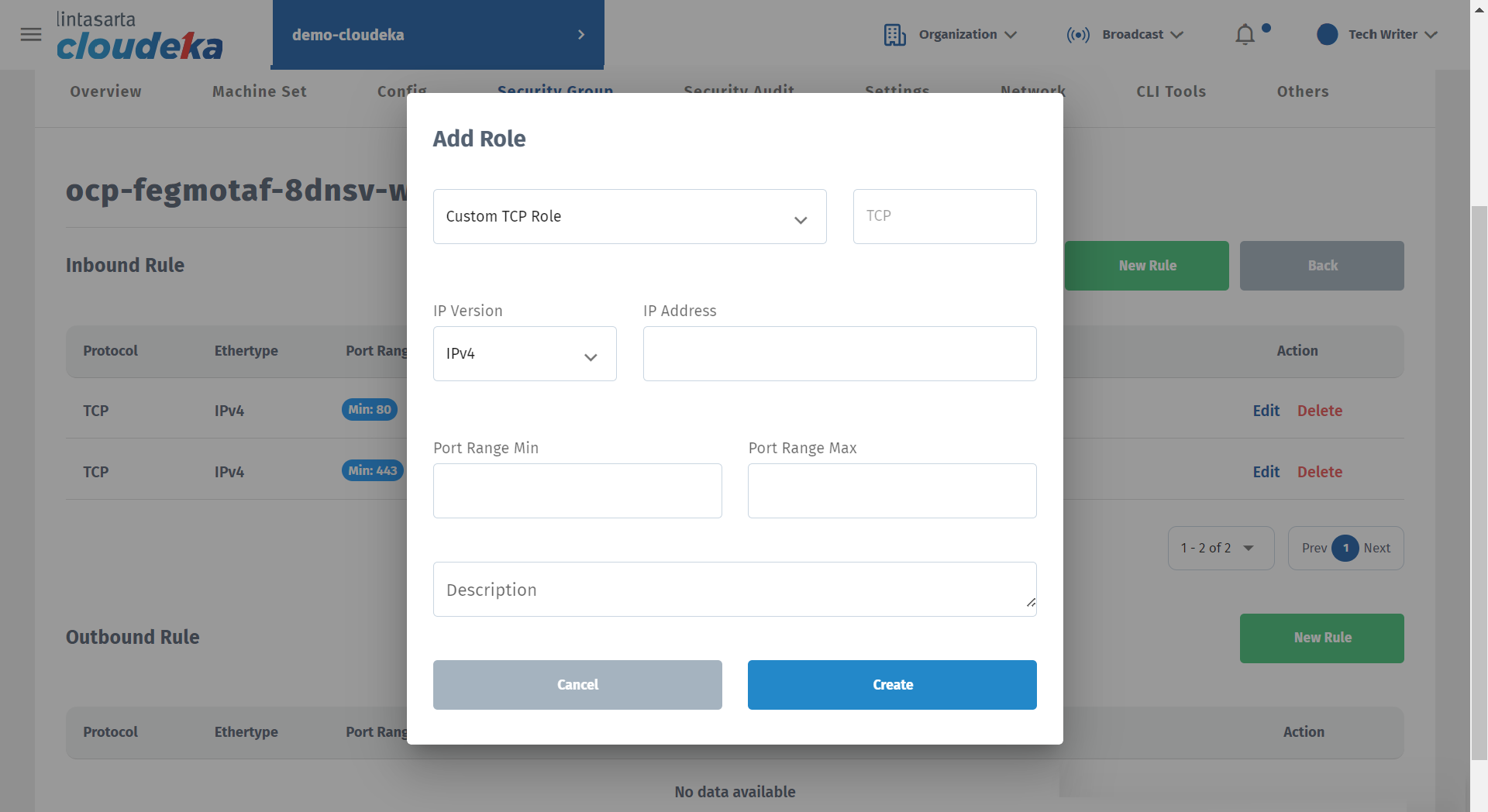
Column
Description
Protocol Type
There are several types of protocols that can be used, including the following: - Custom TCP Role - Custom UDP Role - Custom EDP Role - All ICMP Rule - SSH - HTTP - HTTPS - MySQL - MongoDB - PostgreSQL
IP Version
You can have the IPv4 version or the IPv6 version.
IP Address
The internet protocol address used along with the Network ID to determine the number of bits allocated to networks and hosts in an internet protocol address used.
Port Range Min
Low port number in the allowed range.
Port Range Max
Highest port number in the allowed range.
Description
Displays a description of the configuration of the inbound rule or outbound rule that was created.
Click the Create button if you want to continue creating the firewall or Cancel if you don't want to continue the process.
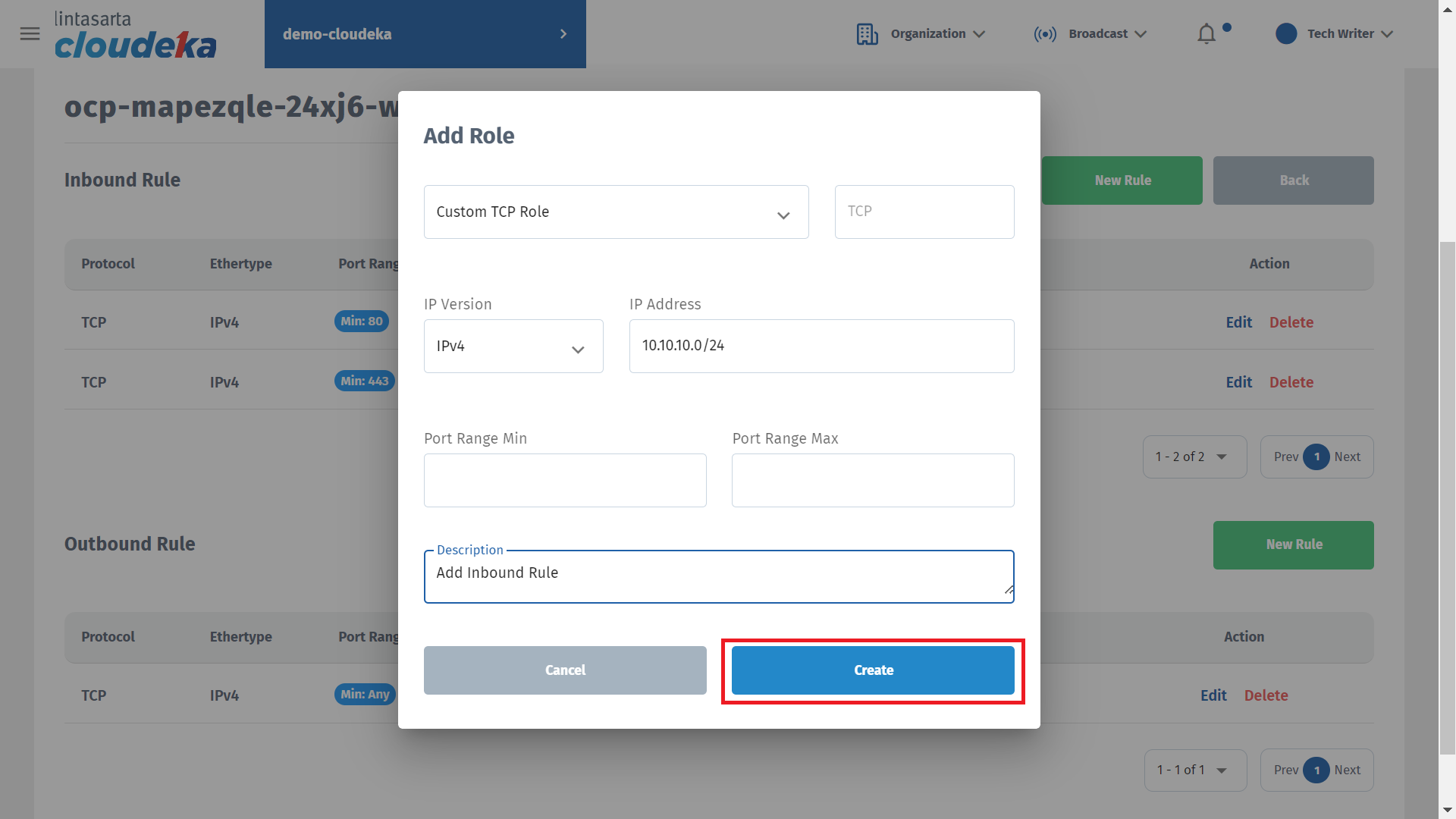
A notification will appear if the creation is successful "Adding the new rule was successful".
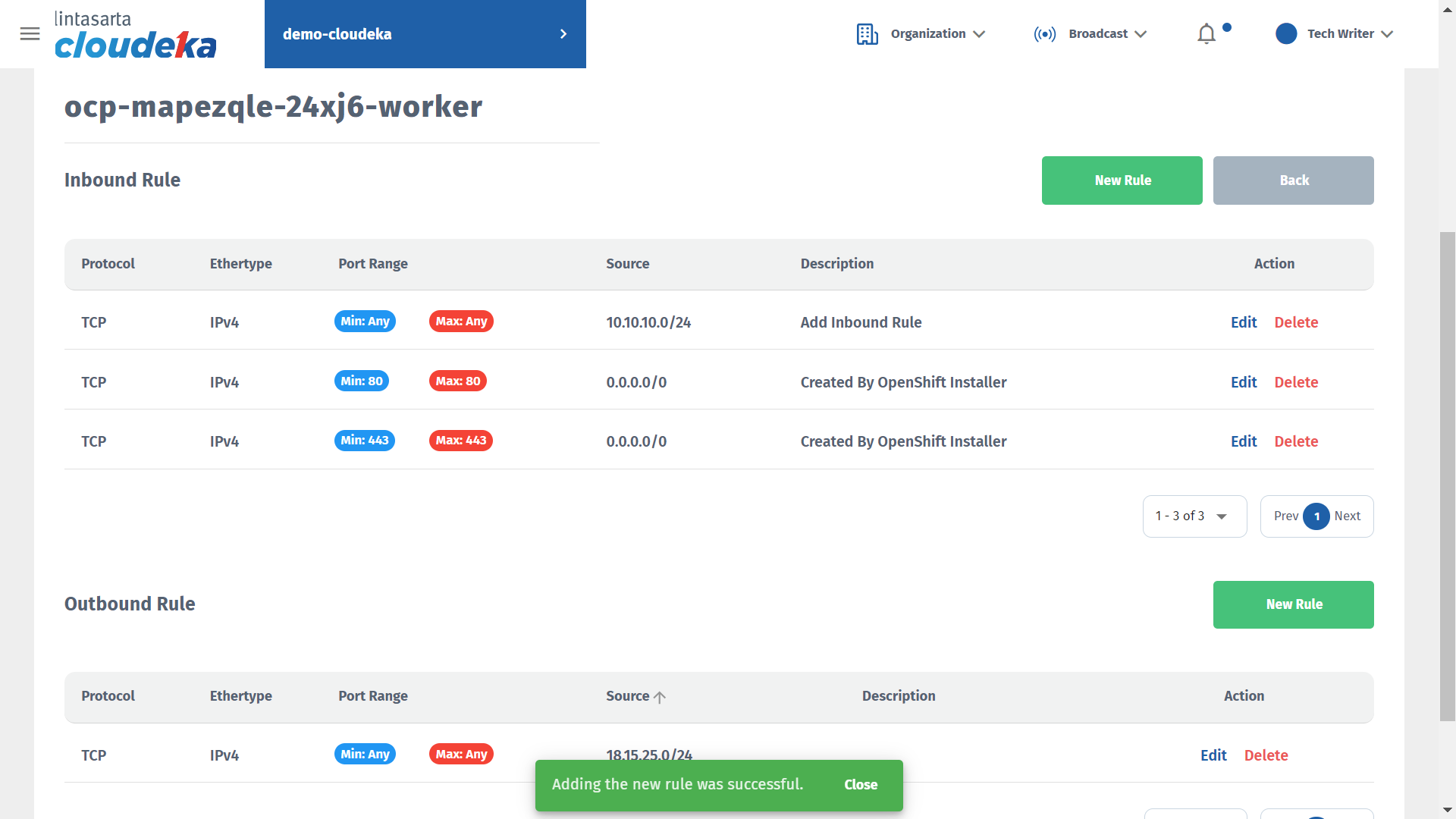
Edit Inbound/Outbound Rule
This guide is used if there is Security Group data that you want to change. Here are the steps to update incoming or outgoing rule data on Deka ROCK:
On the Cloudeka portal service page, select the Deka ROCK menu on the Platform.

Press the More button then select the Details button.

Select the Security Group tab.

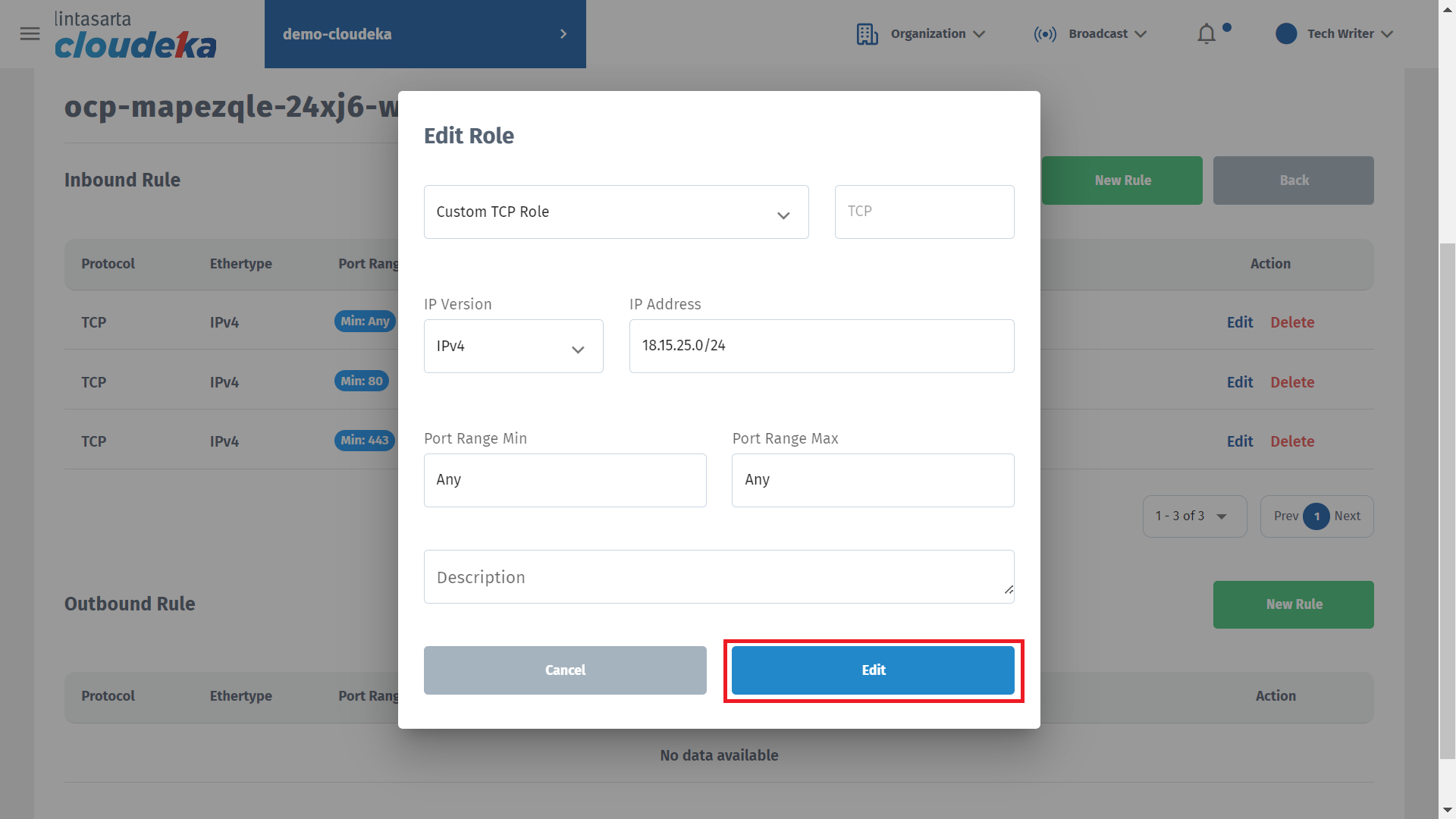
Press the Edit button.
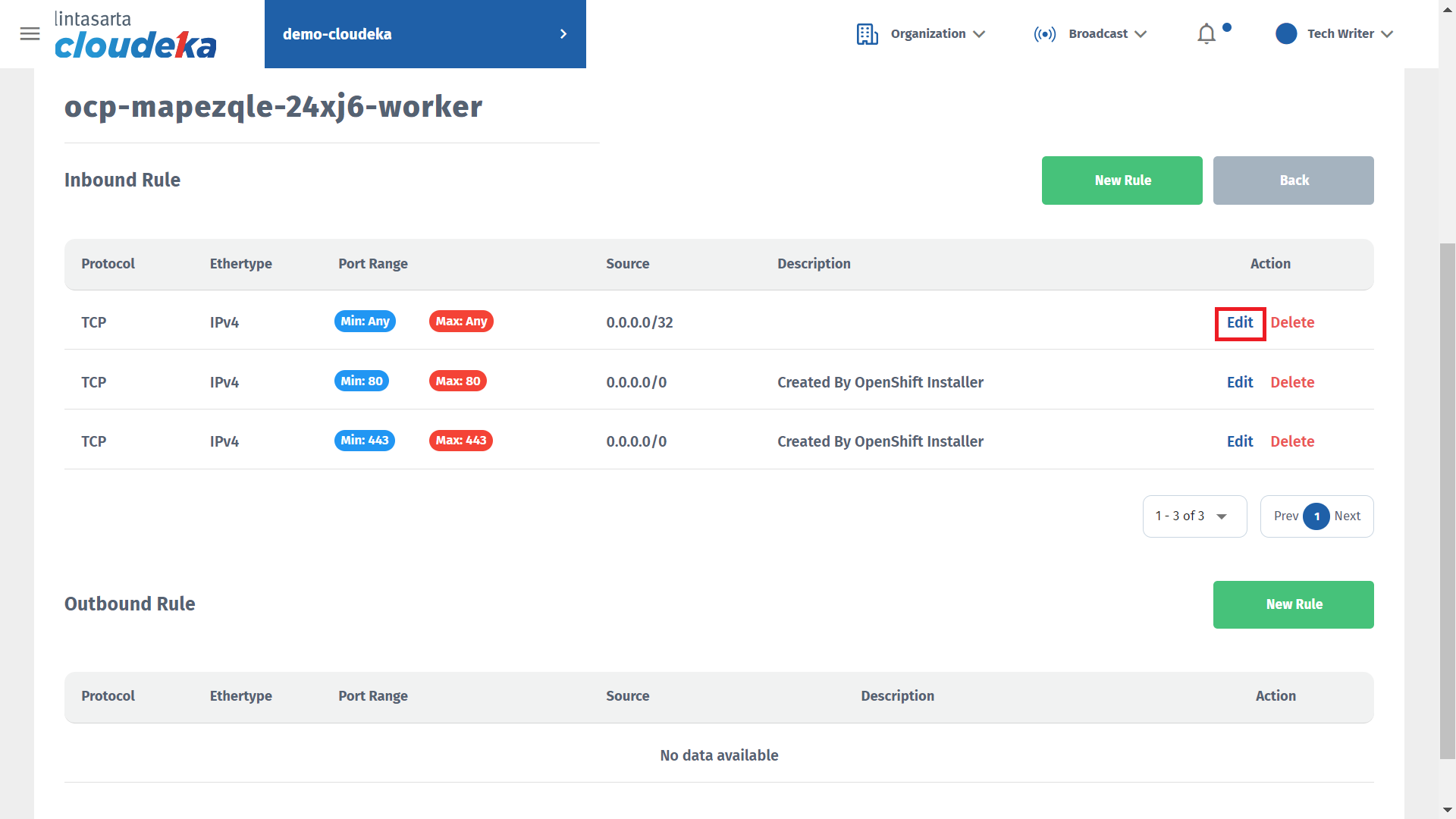
Click the Edit button if you want to save the changes or Cancel if you do not want to continue the process.
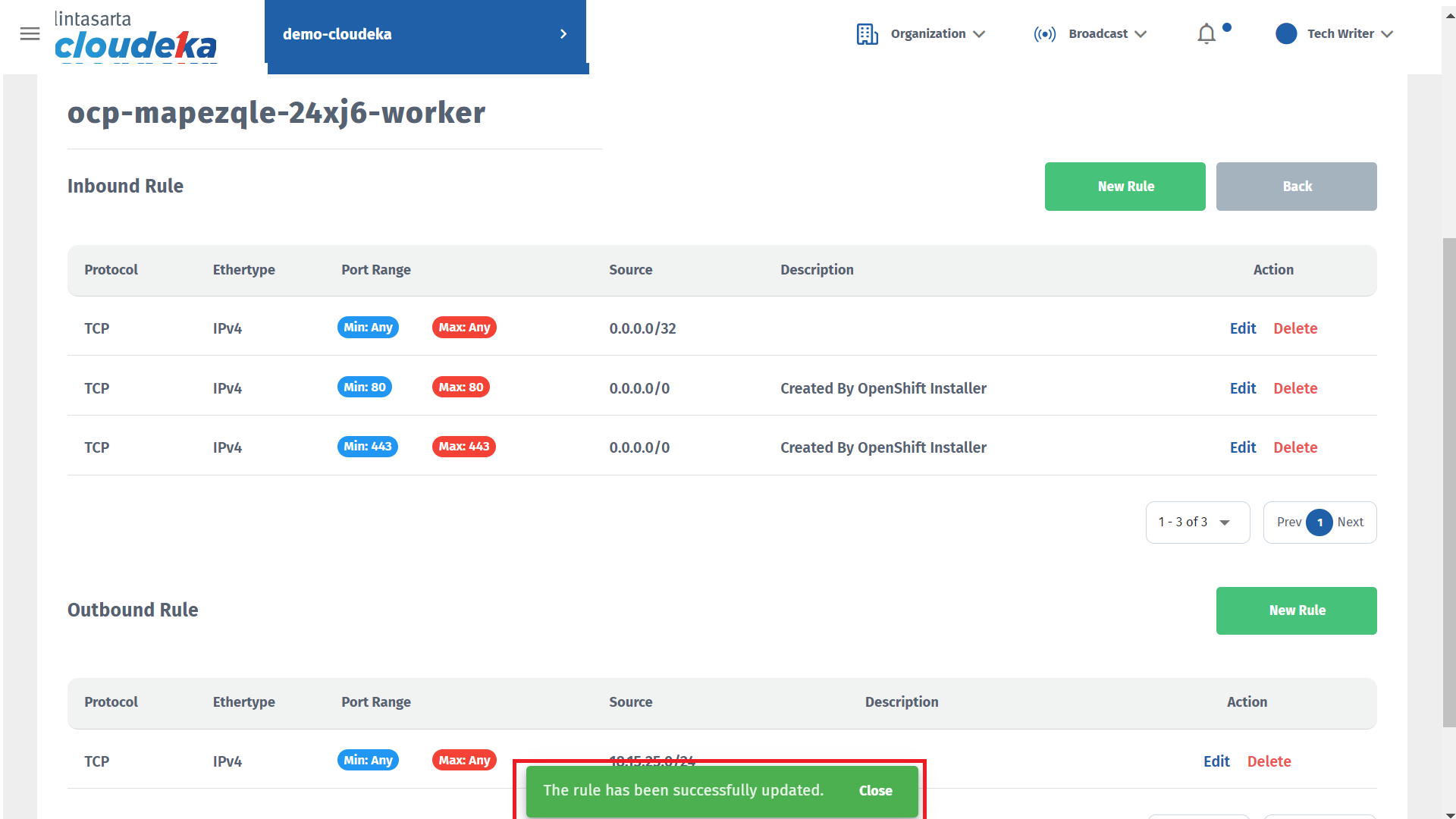
A notification "The rule has been successfully updated" will appear if the data has been successfully updated.
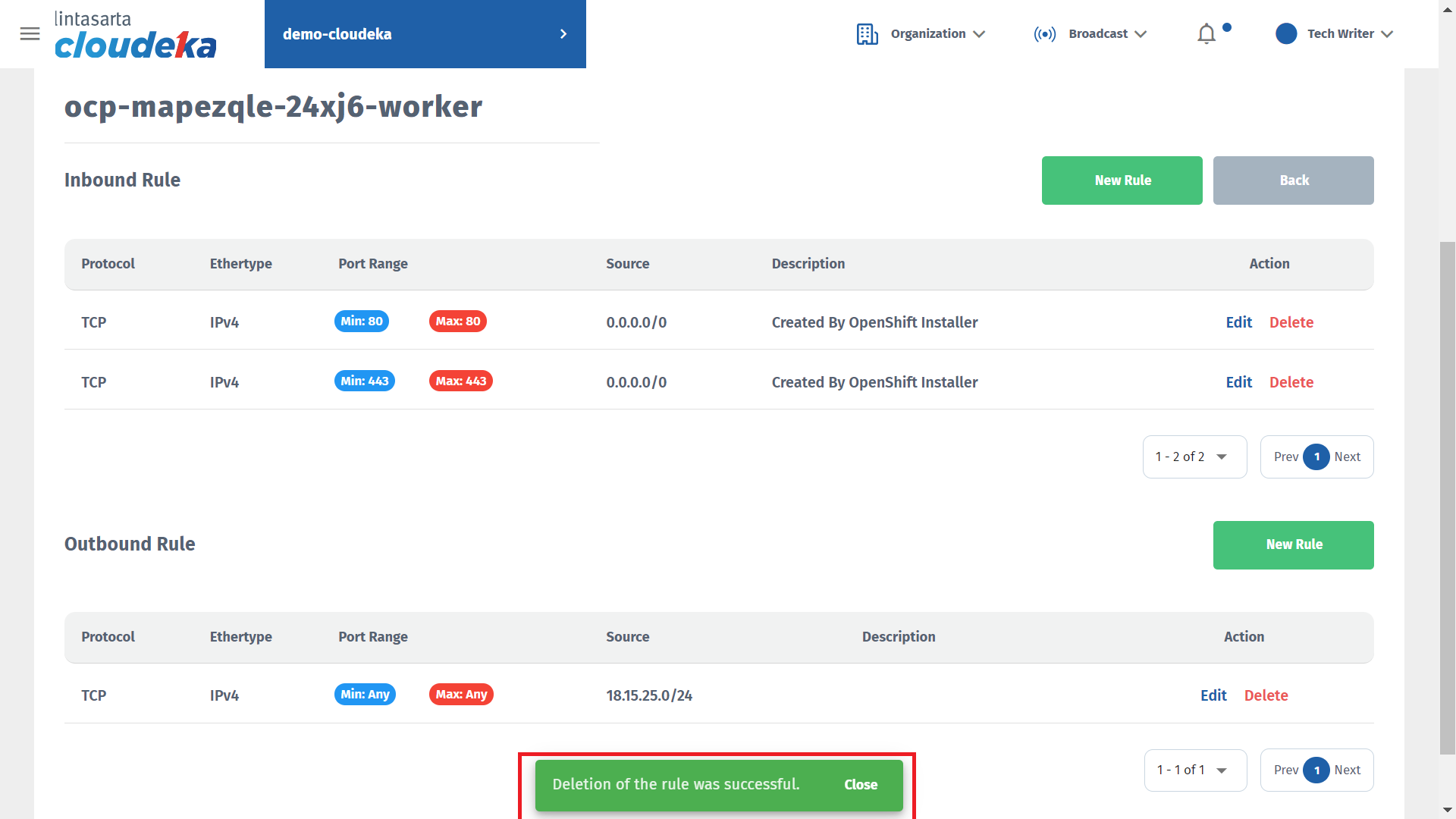
Delete Inbound/Outbound Rule
Following are the steps to delete the incoming or outgoing rule data configuration on Deka ROCK:
On the Cloudeka portal service page, select the Deka ROCK menu on the Platform.

Press the More button then select the Details button.

Select the Security Group tab.

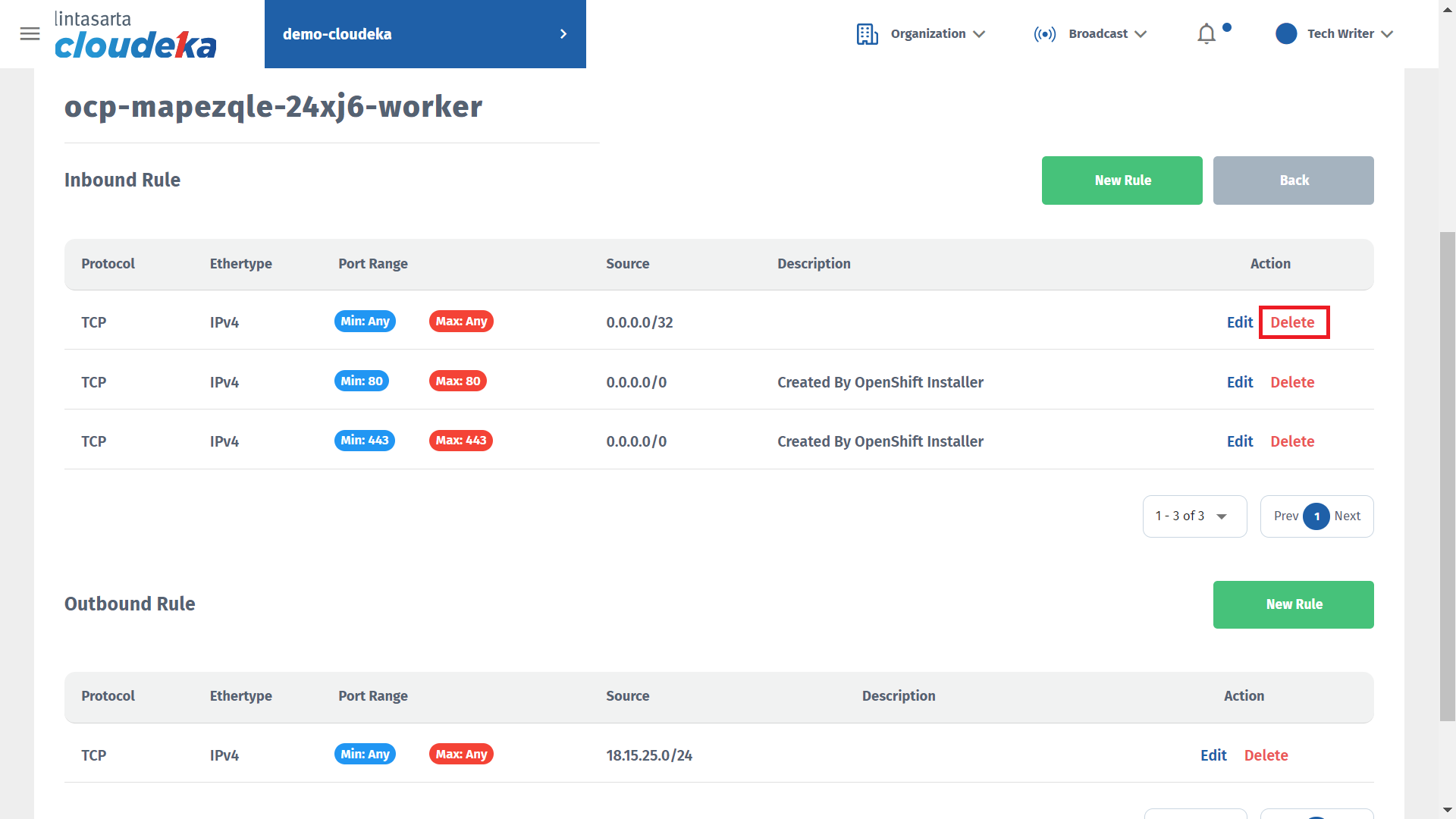
Press the Delete button in the Action column.
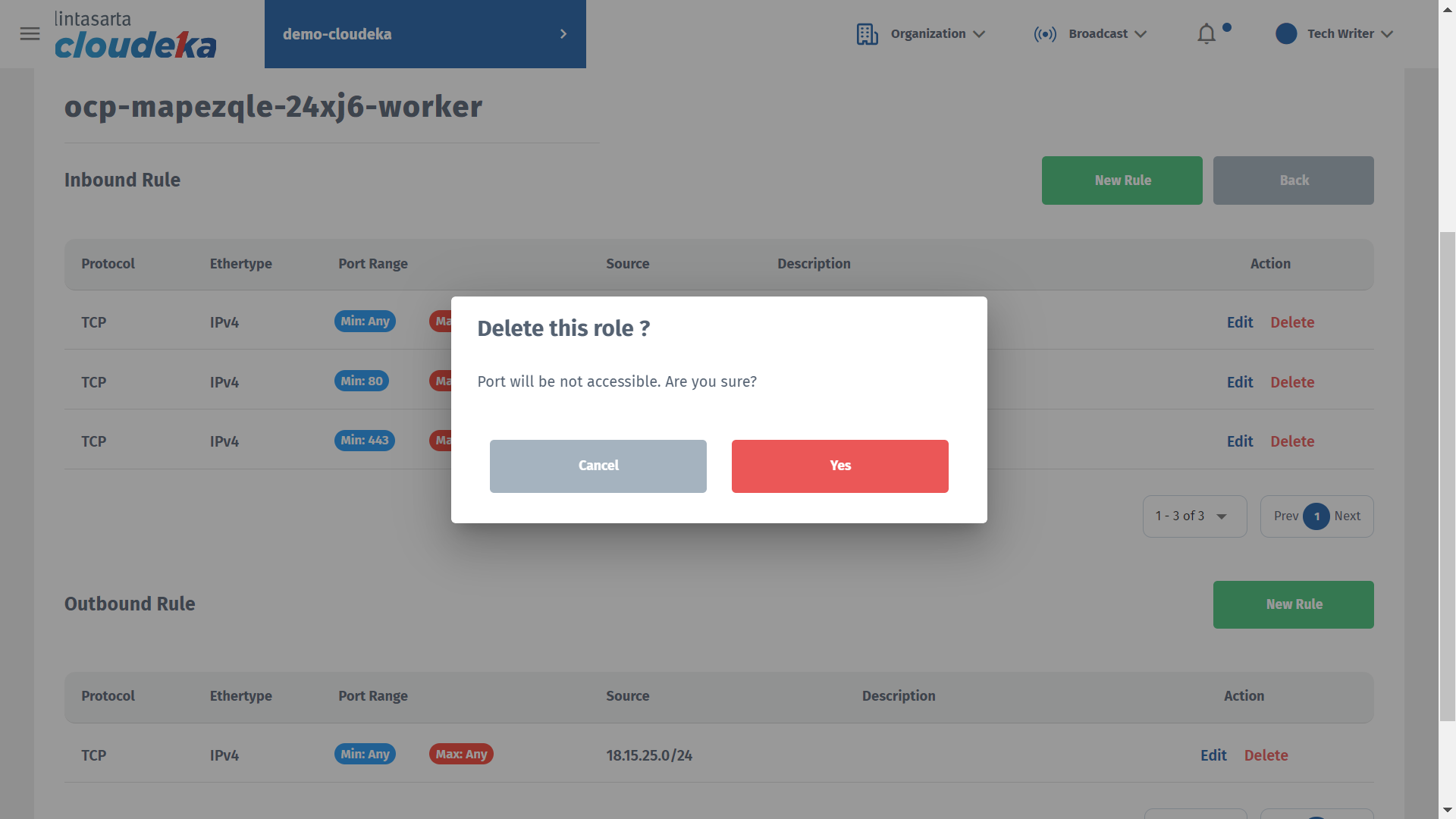
The Delete this Role window appears, click the Yes button to continue the process.
The notification "Deletion of the rule was successful" will appear if it is successfully deleted.
Last updated
